Archive
Change Unix File Permissions Using C
 This is a small program written in C used to change permissions of files in Unix.
This is a small program written in C used to change permissions of files in Unix.
You may ask why would someone want to use a C snippet instead of a quick “chmod” shell script?
Well, a simple “chown” script works just fine for cases where you don’t have a ridiculously large amount of files. Things get painfully slow when besides having millions of files you also have millions of directories. In those rare cases there is nothing faster than C.
If you have a 64 bit operating system you can compile this code with “-m64” flag for better performance.
#include
#include
#include
#include
#define PATH "/export/home/egloo"
#define UID 501
#define GID 501
#define NOTIFICATION_INTERVAL 10000
int file_count = 0;
char cmd[128];
static int callback(const char *fpath, const struct stat *sb, int typeflag) {
// Check if it's a file or a directory
if (typeflag == FTW_D || typeflag == FTW_F) {
// Apply new permissions
chown(fpath, UID, GID);
// Send progress notification
file_count++;
if ( 0 == ( file_count % NOTIFICATION_INTERVAL ) ){
fprintf( stderr, "%ld\n", file_count );
sprintf(cmd,"/bin/echo \"%i files processed\" | /bin/mail -s \"CHOWN PROGRESS\" user@domain.com", file_count);
system(cmd);
}
}
// Continue FTW
return 0;
}
int main(int argc, char **argv) {
ftw(PATH, callback, 256);
}
Make GNOME use Xscreensaver instead of Gnome Screensaver
 As you may know, Gnome comes preinstalled with a few catalog of basic screensavers: Gnome Screensaver which is the default screen saver and locker in a Gnome desktop. It is designed with simplicity and security in mind.
As you may know, Gnome comes preinstalled with a few catalog of basic screensavers: Gnome Screensaver which is the default screen saver and locker in a Gnome desktop. It is designed with simplicity and security in mind.
For this reason many useres prefer to use xscreensaver wich is a better, more secure and universally accepted screensaver program for Unix-like operating systems.
In fact xscreensaver can be found installed by default on some Linux distributions like Ubuntu and latest versions of SUSE, but there are still Red Hat based systems that do not install this packages.
To install xscreensaver you can use the standard repositories from your specific OS.
Red Hat based:
su -c "yum install xscreensaver"
Debian based:
sudo apt-get install xscreensaver
Now xscreensaver is installed, we launch the configuration screen by typing xsreensaver-demo on a console or by clicking on System > Preferences > Look and Feel > Screensaver. This will pop a message asking you to deactivate the gnome-screensaver daemon which should be fine.
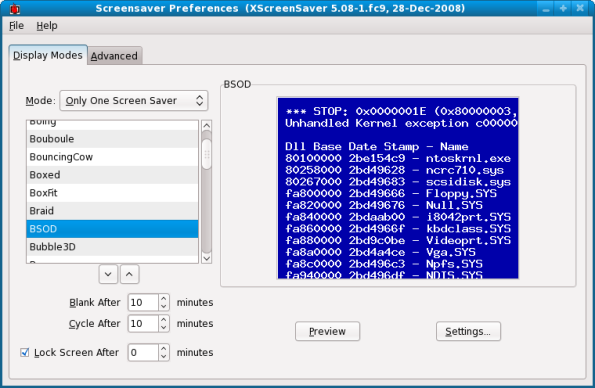
Select the screensaver design of your choice, hit the Preview button and close the dialog box when you’re done.
At this point, the screensaver should lock automatically after the defined inactive time, BUT it wont work if you want to activate it manally by pressing Ctrl+Alt+L or System > Lock Screen. This is because even when you defined xscreensaver as the default application, gnome is still looking for the old daemon in order to activate the screensaver.
To solve this problem open a terminal as root and issue the following command:
ln -sf /usr/bin/xscreensaver-command \
/usr/bin/gnome-screensaver-command
Now you can lock your screen and start xscreensaver with the standard gnome commands. 🙂
Connect Through SSH Without a Password
 One day, you will find yourself trying to execute a command on a remote UNIX box without the need of typing the password. The basis of using this technique relies on public keys which are a kind of digital signatures.
One day, you will find yourself trying to execute a command on a remote UNIX box without the need of typing the password. The basis of using this technique relies on public keys which are a kind of digital signatures.
Let’s supose we have a server named “Mailserver” and another server called “Monitor” and you want Monitor to connect every 30 minutes to Mailserver and verify the health of some services.
Anyway, here is the quick-guide:
First of all connect to Monitor with the user of you choice.
Then, type:
ssh-keygen -t rsa
This command will create the RSA public key of the current user. You will be asked to type a passphrase but it’s not necesary at all; You can just ignore it.
When the command finishes execution, a message will appear telling you the location of the new files. In most cases it is placed in the .ssh/ directory inside your home/ path.
Next, you’ll have to copy the public they to the authorized_keys2 file on the remote server (in this case Mailserver). To make it simple, here is the command (Remember to substitute user and hostname with your own):
scp ~/.ssh/id_rsa.pub user@hostname:~/.ssh/authorized_keys2
This will the last time you’ll prompted to type the password. When the transfer finishes, you should be able to ssh from Monitor to Mailserver without being prompted for a pass. 🙂
NOTE: On some UNIX like Solaris the default location of the public-keys can vary from system to system.
NOTE 2: You must have RSAAuthentication yes in your /etc/ssh/sshd_config file. On many Linux installations this setting is commented out in a default install.
How to Read MySQL Binary Logs
 MySQL database server utilizes a transaction log to track all of the modifications performed within the databases. This log ensures both that the database is able to recover when abruptly interrupted (such as a loss of power) and that users are able to undo (or “rollback” in database language) the results of a database transaction. Except for the cases where the administrator has disabled or commented out the log-bin parameter in my.cfg file, this log is generated by default. As the name implies, binary log (transaction log) files are written in binary format, but sometimes you may need to examine the content of the transaction logs in text format, where the mysqlbinlog utility will come in handy.
MySQL database server utilizes a transaction log to track all of the modifications performed within the databases. This log ensures both that the database is able to recover when abruptly interrupted (such as a loss of power) and that users are able to undo (or “rollback” in database language) the results of a database transaction. Except for the cases where the administrator has disabled or commented out the log-bin parameter in my.cfg file, this log is generated by default. As the name implies, binary log (transaction log) files are written in binary format, but sometimes you may need to examine the content of the transaction logs in text format, where the mysqlbinlog utility will come in handy.
A binlog file normally is named hostname-bin.xxxxx and stored in /var/lib/mysql directory. It cannot be opened and read straight away as it’s a binary file so we can make use of mysqlbinlog command.
For example, to display the contents of the binary log file named localhost-bin.000004, use this command:
mysqlbinlog localhost-bin.000004
The output includes all events contained in localhost-bin.000004. Event information includes the statement executed, the time the statement took, the thread ID of the client that issued it, the timestamp when it was executed, and so forth.
The binlogs are likely to be very huge thus making it almost impossible to read anything on screen. However, you can pipe the output into a file which can be open up for later browsing in text editor:
mysqlbinlog localhost-bin.000004 > filename.txt
To reduce the amount of data retrieved from binary logs, there are several options that can be used to limit the data that is been returned. Among the useful ones are listed below:
–start-datetime=[DATETIME]
–stop-datetime=[DATETIME]
The datetime value is relative to the local time zone on the machine where you run mysqlbinlog. The value should be in a format accepted for the DATETIME or TIMESTAMP data types. For example:
mysqlbinlog --start-datetime="2008-05-22 00:00:00" --stop-datetime="2008-05-29 00:00:00" localhost-bin.000004
For more information, you can take a look at the official mysqlbinlog documentation.
Share Keyboard and Mouse with Synergy
 It’s very usual for a Linux user to work with multiple monitors and machines; It gives a lot of flexibility and a big boost to our performance. But switching between the different keyboards and mice can be a bit tedious.
It’s very usual for a Linux user to work with multiple monitors and machines; It gives a lot of flexibility and a big boost to our performance. But switching between the different keyboards and mice can be a bit tedious.
For this purpose there is a hardware device that allows you to control multiple computers from a single keyboard, video monitor and mouse: a KVM switch. KVM switches are today difficult to find and not very cheap.
Fortunately there is a software approach to KVM switches: Synergy.
Synergy is used in situations where several PCs are used together, with a monitor connected to each, but are to be controlled by one user. You need only one keyboard and mouse on the desk.
Synergy runs on Windows, Linux and MacOS X in command line mode. There are also some cool GUIs like SynergyKM for MacOS X, QuickSynergy for Linux and MacOS X, and the self Synergy GUI for Windows.
The configuration can be done from the command line but trust me, having such great and minimalistic GUIs out there you don’t want to do that.

Okay, okay the main reason why this blog entry does not cover the internal commands is because there is already an excellent documentation that explains step by step the commands you can use with Synergy… You know, why reinventing the wheel.
Linux Cached Memory
 In Linux, reading from a disk is very slow compared to accessing real memory. In addition, it is common to read the same part of a disk several times during relatively short periods of time. For example, one might first read an e-mail message, then read the letter into an editor when replying to it, then make the mail program read it again when copying it to a folder. Or, consider how often the command ls might be run on a system with many users. By reading the information from disk only once and then keeping it in memory until no longer needed, one can speed up all but the first read. This is called disk buffering, and the memory used for the purpose is called the buffer cache.
In Linux, reading from a disk is very slow compared to accessing real memory. In addition, it is common to read the same part of a disk several times during relatively short periods of time. For example, one might first read an e-mail message, then read the letter into an editor when replying to it, then make the mail program read it again when copying it to a folder. Or, consider how often the command ls might be run on a system with many users. By reading the information from disk only once and then keeping it in memory until no longer needed, one can speed up all but the first read. This is called disk buffering, and the memory used for the purpose is called the buffer cache.
Unlike Windows other operating systems, Linux administers memory the smartest way it can.
Since unused memory is next to worthless, the filesystem takes whatever memory is left and caches it in order to speed up disk access. When the cache fills up, the data that has been unused for the longest time is discarded and the memory thus freed is used for the new data.
Whenever an application needs memory, the kernel makes the cache smaller; You do not need to do anything to make use of the cache, it happens completely automatically.
Freeing memory buffer does not make your programs faster… Actually it makes disk access slower.
BUT if for some reason (kernel debugging for example) you want to force the buffer to be freed, you need to set the drop_caches value to 1:
$ echo 1 > /proc/sys/vm/drop_caches
Issuing this command will release all the cached memory and also will stop collecting I/O buffer blocks. Let’s see an example of the effect:

Under normal situations, most of the memory is already cached by the system. But if we force the system to free the memory, you can see in the graph how the memory is suddenly dropped.
The technical details of how this works are explained on the Linux API
FTP Error Codes
![]() In case you are a die-hard FTP user, you should find helpful the error code reference. Normally, these codes appear in the system log files, or directly into your terminal.
In case you are a die-hard FTP user, you should find helpful the error code reference. Normally, these codes appear in the system log files, or directly into your terminal.
120 Service ready in nnn minutes.
125 Data connection already open; transfer starting.
150 File status okay; about to open data connection.
200 Command okay.
202 Command not implemented, superfluous at this site.
211 System status, or system help reply.
212 Directory status.
213 File status.
214 Help message.On how to use the server or the meaning of a particular non-standard command. This reply is useful only to the human user.
120 Service ready in nnn minutes.
125 Data connection already open; transfer starting.
150 File status okay; about to open data connection.
200 Command okay.
202 Command not implemented, superfluous at this site.
211 System status, or system help reply.
212 Directory status.
213 File status.
214 Help message.On how to use the server or the meaning of a particular non-standard command. This reply is useful only to the human user.
215 NAME system type. Where NAME is an official system name from the list in the Assigned Numbers document.
220 Service ready for new user.
221 Service closing control connection.
225 Data connection open; no transfer in progress.
226 Closing data connection. Requested file action successful (for example, file transfer or file abort).
227 Entering Passive Mode (h1,h2,h3,h4,p1,p2).
230 User logged in, proceed. Logged out if appropriate.
250 Requested file action okay, completed.
257 “PATHNAME” created.
331 User name okay, need password.
332 Need account for login.
350 Requested file action pending further information
421 Service not available, closing control connection.This may be a reply to any command if the service knows it must shut down.
425 Can’t open data connection.
426 Connection closed; transfer aborted.
450 Requested file action not taken.
451 Requested action aborted. Local error in processing.
452 Requested action not taken. Insufficient storage space in system.File unavailable (e.g., file busy).
500 Syntax error, command unrecognized. This may include errors such as command line too long.
501 Syntax error in parameters or arguments.
502 Command not implemented.
503 Bad sequence of commands.
504 Command not implemented for that parameter.
530 Not logged in.
532 Need account for storing files.
550 Requested action not taken. File unavailable (e.g., file not found, no access).
551 Requested action aborted. Page type unknown.
552 Requested file action aborted. Exceeded storage allocation (for current directory or dataset).
553 Requested action not taken. File name not allowed.NAME system type. Where NAME is an official system name from the list in the Assigned Numbers document.
220 Service ready for new user.
221 Service closing control connection.
225 Data connection open; no transfer in progress.
226 Closing data connection. Requested file action successful (for example, file transfer or file abort).
227 Entering Passive Mode (h1,h2,h3,h4,p1,p2).
230 User logged in, proceed. Logged out if appropriate.
250 Requested file action okay, completed.
257 “PATHNAME” created.
331 User name okay, need password.
332 Need account for login.
350 Requested file action pending further information
421 Service not available, closing control connection.This may be a reply to any command if the service knows it must shut down.
425 Can’t open data connection.
426 Connection closed; transfer aborted.
450 Requested file action not taken.
451 Requested action aborted. Local error in processing.
452 Requested action not taken. Insufficient storage space in system.File unavailable (e.g., file busy).
500 Syntax error, command unrecognized. This may include errors such as command line too long.
501 Syntax error in parameters or arguments.
502 Command not implemented.
503 Bad sequence of commands.
504 Command not implemented for that parameter.
530 Not logged in.
532 Need account for storing files.
550 Requested action not taken. File unavailable (e.g., file not found, no access).
551 Requested action aborted. Page type unknown.
552 Requested file action aborted. Exceeded storage allocation (for current directory or dataset).
553 Requested action not taken. File name not allowed.
Using a Video Projector with Linux
 One of the first problems a user faces is the need to show topics and presentations with the help of a video projector and a laptop running Linux.
One of the first problems a user faces is the need to show topics and presentations with the help of a video projector and a laptop running Linux.
For some reason beyond me, Linux newcomers get turned off by the mere mention of a command line. The whole concept of using a console is like alien.
…
Okay, there are two options: You can try to modify your Xorg.conf file until you mess it up, destroy your computer’s GUI, and get attacked by sharks (Let’s be honest, this is not worth the effort for just a single presentation), or you can go for a fast, secure and temporary on-the-fly screen resizing.
If you chose the second options, keep reading. This was tested on my HP Pavilion dv2000, with a standard VGA port, running Fedora 9 x86_64.
First some easy stuff (OPTIONAL STEP): let’s disable the screensaver and as we want our screen to be ready and visible throughout the presentation.
$ xset s off
Next we have to take care of the external output. The command here is xrandr, which stands for “X Resize And Rotate” and is used to “allow clients to dynamically change X screens, so as to resize, rotate and reflect the root window of a screen“.
On your console type xrandr -v to check if the package is installed (99% chance it is).
$ xrandr -v
Server reports RandR version 1.2
Now, connect the video projector to the laptop. And automagically you should see… nothing, since the screens are not yet configured.
In order to verify it the system recognized the device, lets query the connected screens with the command xrandr -q
$ xrandr -q
You should see something like the following:
LVDS: minimum 320 x 200, current 1280 x 800, maximum 1280 x 800
VGA connected 1920x1440+0+0 (normal left inverted right x axis y axis) 380mm x 285mm
As you can see, there is a device named LVDS which is the “Low-voltage differential signaling” for the laptop panel, and there is also a VGA device which represents our video projector.
Here you can use the same resolution on the laptop screen and the projector or using two different resolutions. The first approach is a little less prone to errors so we are going to use it.
To clone the screen:
$ xrandr --output LVDS --auto --output VGA --auto --same-as LVDS
To extend the screen to the right in the VGA projector:
$ xrandr --output LVDS --auto --output VGA --auto --right-of LVDS
And finally, to turn off projection:
$ xrandr --output VGA --off
This method can also be used with DVI and S-VIDEO cables. Just be sure to type the correct name of the output device as it is showed with the xrandr command.
Path of the Linux Jedi
 If you really want to get your hands on the “dirty job” and become a serious Linux programmer, I really recommend you to read the following book.
If you really want to get your hands on the “dirty job” and become a serious Linux programmer, I really recommend you to read the following book.
It’s called Advanced Linux Programming and is distributed under the GNU General Public License so you’re free to copy, share, and most important: read it.
As the publisher says, this book will help you to:
Develop GNU/Linux software that works the way users expect it to.
Write more sophisticated programs with features such as multiprocessing, multi-threading, interprocess communication, and interaction with hardware devices.
Improve your programs by making them run faster, more reliably, and more securely.
Understand the preculiarities of a GNU/Linux system, including its limitations, special capabilities, and conventions.
If you’re a developer already experienced with programming for the GNU/Linux system, are experienced with another UNIX-like system and are interested in developing GNU/Linux software, or want to make the transition for a non-UNIX environment and are already familiar with the general principles of writing good software, this book is for you. In addition, you will find that this book is equally applicable to C and C++ programming. Even those progamming in other languages will find this book useful since the C language APIs and conventions are the lingua franca of GNU/Linux.
As an advice, you will need a solid grasp of C programming knowledge.
Thruth be told, good luck.
Turn off echo in a terminal
![]() Imagine you are writing a shell script that requires the user to input confidential information, lets say a password.
Imagine you are writing a shell script that requires the user to input confidential information, lets say a password.
The user wont feel comfortable if the password is echoed on the screen like a simple text. If you ever used expect interactive scripting, you know for sure this kind of problem.
Don’t worry, its amazingly easy to perform this trick and stop echoing whatever the user types on the screen.
Simply add the following line to your script:
stty -echo
and you are done. The stty output will go offline. Let’s see an example:
#!/bin/bash
echo Hello
stty -echo
# do what ever you want to do
echo 'I slept with your girlfriend'
stty echo
echo Bye
exit 0;
That’s it! Just remember to put it back to normal with the following command:
stty echo
Also, it would be helpful for you to read the whole man page for stty.
$ man stty